Using cloud security, you will attain the control and assurance that you need to run your business with the most adaptable and secure cloud computing needs available today. AWS data center and networked architecture help to protect you in terms of the following:
Cloud security services allow you to automate manual security tasks so you can turn your focus to rising and innovating your business.

Imperial Cloud Services And Data Center Providers offer a shared responsibility model. Our cloud services address cloud security for its infrastructure, while your organization is trustworthy for ensuring your data and workloads. Amazon provides a range of security services and features, which includes
A breach of standards and regulations is another essential part of security since a mistake can be costly for your organization.
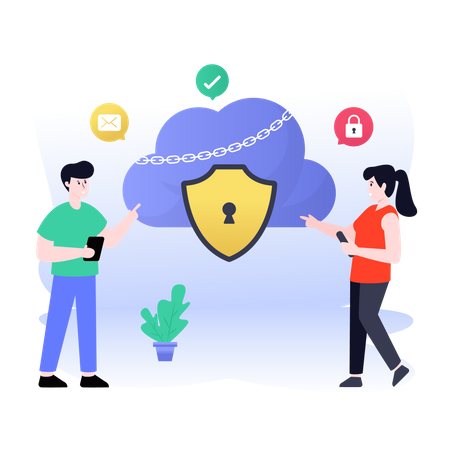
Our Cloud security services are devised to assist you in building secure, high-performing, and efficient infrastructure for your applications. Our security services and solutions are concentrated on delivering the following key strategic benefits:
We build and maintain our general preference for creative security services, which can aid you in facilitating your security and regulatory conditions.

Automating security assignments on AWS helps you to be better protected by decreasing human configuration mistakes and giving your team more time to concentrate on other work critical to your business. You can control who can access your data, where your data is stored, and what resources your organization consumes at any moment. Fine-grain identity and access control integrated with constant monitoring for near real-time security information confirms that the right resources have the proper access at all times, wherever your data is stored.

Cloud conditions can be complicated, consisting of many technologies and strategies. At the same time, they're revealed to a vast range of threats. Hence, you will not find a one-size- fits-all cloud security service in which most of its services tackle specific areas. Some of the most common cloud security services such as:


The Cloud Readiness Assessment is a phase in which your company studies its resources and IT environment to resolve if it can migrate to the Cloud.

Solution Designing creates customized blueprints based on the AWS Well-Architected Framework and prebuilt them based on the reference architectures.

Investing in the Cloud or companies that run, supply, or have business models on the internet is essential to consider the business model and growth potential.

Migration planning is the essential first step in a successful data migration project to determine, prepare, extract, convert, and transfer data of the proper form and quality.

A proof of concept focuses on the viability of a project, so you can decide whether your idea is worth pursuing and what might be required to bring the vision to realization.

Live migration lets Google Cloud performs maintenance without interrupting a workload, rebooting a VM, or modifying any of the VM's properties.

Cloud Optimization and Migration provide an objective third-party strategy and toolset for designing the classic business case for moving app workloads to a business cloud.
Data backup is reproducing files to be stored at a selected location. Data recovery is a system that allows restore those files following a disaster.
Designing and documenting the future state of your application is a crucial success factor, and it is an opportunity to optimize the application even in cases where the architecture is not anticipated to change.
Organizations today require a unified information architecture – for information management and analytics, that enables it to leverage all types of data, can address a range of analytics needs, as situations demand, to satisfy business needs. Organizations today require a unified information architecture – for information management and analytics, that enables it to leverage all types of data, can address a range of analytics needs, as situations demand, to satisfy business needs.
Imperial cloud service and data center providers are full-fledged consultants in AWS cloud migration, development, and optimization.